Ransomware is the most common cyber threat Canadians face and it is on the rise.
During a ransomware attack, cybercriminals use malicious software to encrypt, steal, or delete data, then demand a ransom payment to restore it.
Ransomware can have severe impacts including core business downtime, permanent data loss, intellectual property theft, privacy breaches, reputational damage and expensive recovery costs.
Basic cyber security practices would prevent the vast majority of ransomware incidents in Canada.
This page offers resources from the Cyber Centre to help Canadians and Canadian organizations understand the ransomware threat and take action to protect themselves.
Reports
Ransomware case study: the Conti group
This case study describes the typical methods of the Conti ransomware group, one the most prolific cybercriminal groups in operation.
Even by ransomware standards, Conti is regarded as one of the most ruthless and damaging gangs, frequently targeting hospitals, medical networks and other critical services.
In a typical attack Conti actors steal, encrypt and/or delete files. They also threaten to leak sensitive data if the ransom is not paid, a tactic known as “double extortion.”
A typical Conti ransomware attack takes place in four stages: reconnaissance, intrusion, infection and impact.
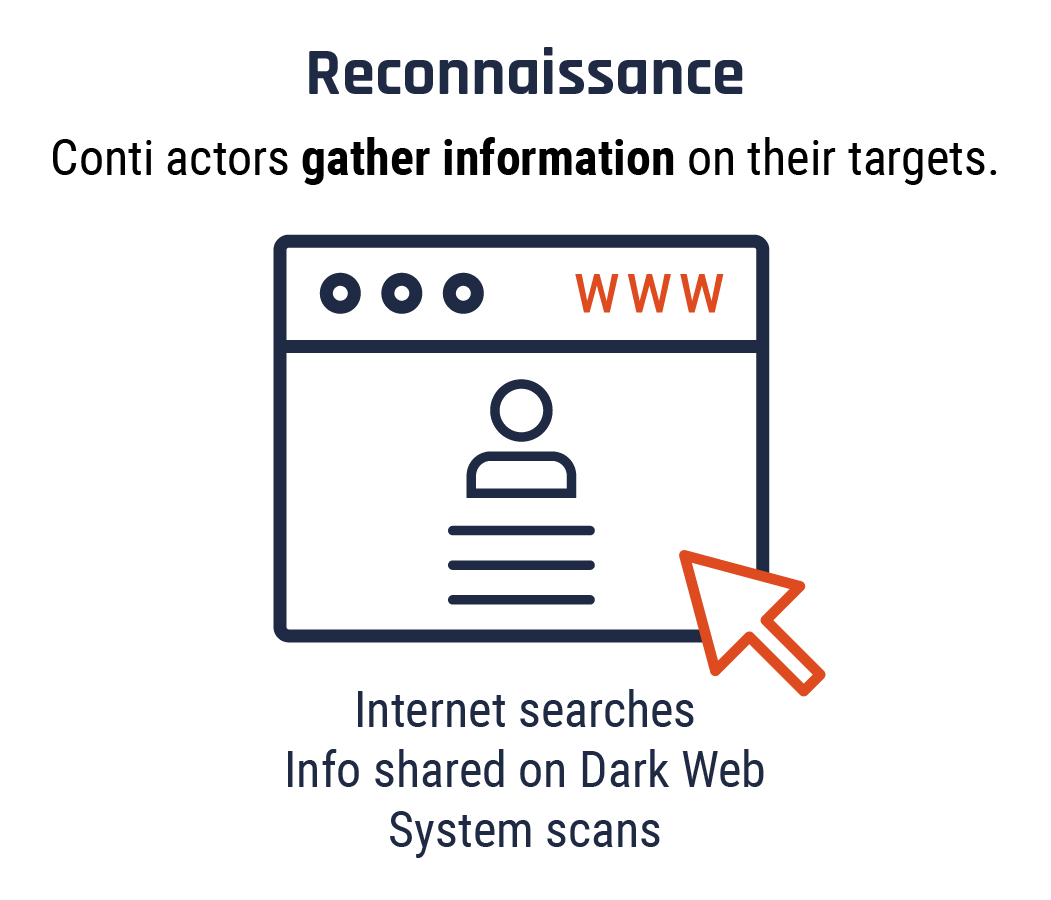
Long description - Stage 1: Reconnaissance
Conti actors gather information to identify high-value targets such as hospitals and other organizations that provide essential services or hold sensitive data. They use Internet searches, system scans and information shared on the Dark Web, such as stolen passwords or login credentials. Conti actors continue to gather information throughout the attack cycle to leverage greater ransoms and to ensure payment is not withheld. Footnote 1
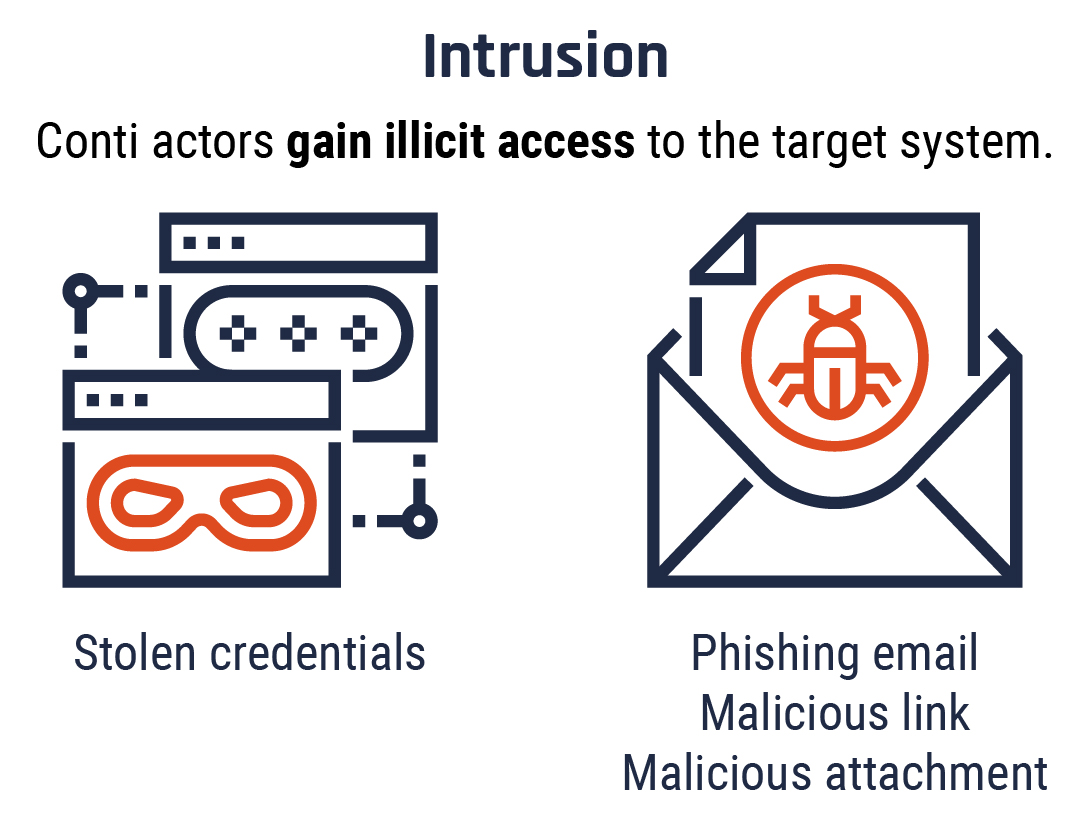
Long description - Stage 2: Intrusion
Conti actors typically gain illicit access to the victim’s system either through stolen credentials or through spear phishing emails containing malicious attachments or links. Unlike generic phishing attempts, spear phishing emails are personalized to the recipient, making them more convincing.
Often the malicious attachment appears to be a regular file type, such as Word, Excel or PDF, but when the victim opens it, malware, such as TrickBot, IcedID, or BazarLoader, downloads and executes on their device.
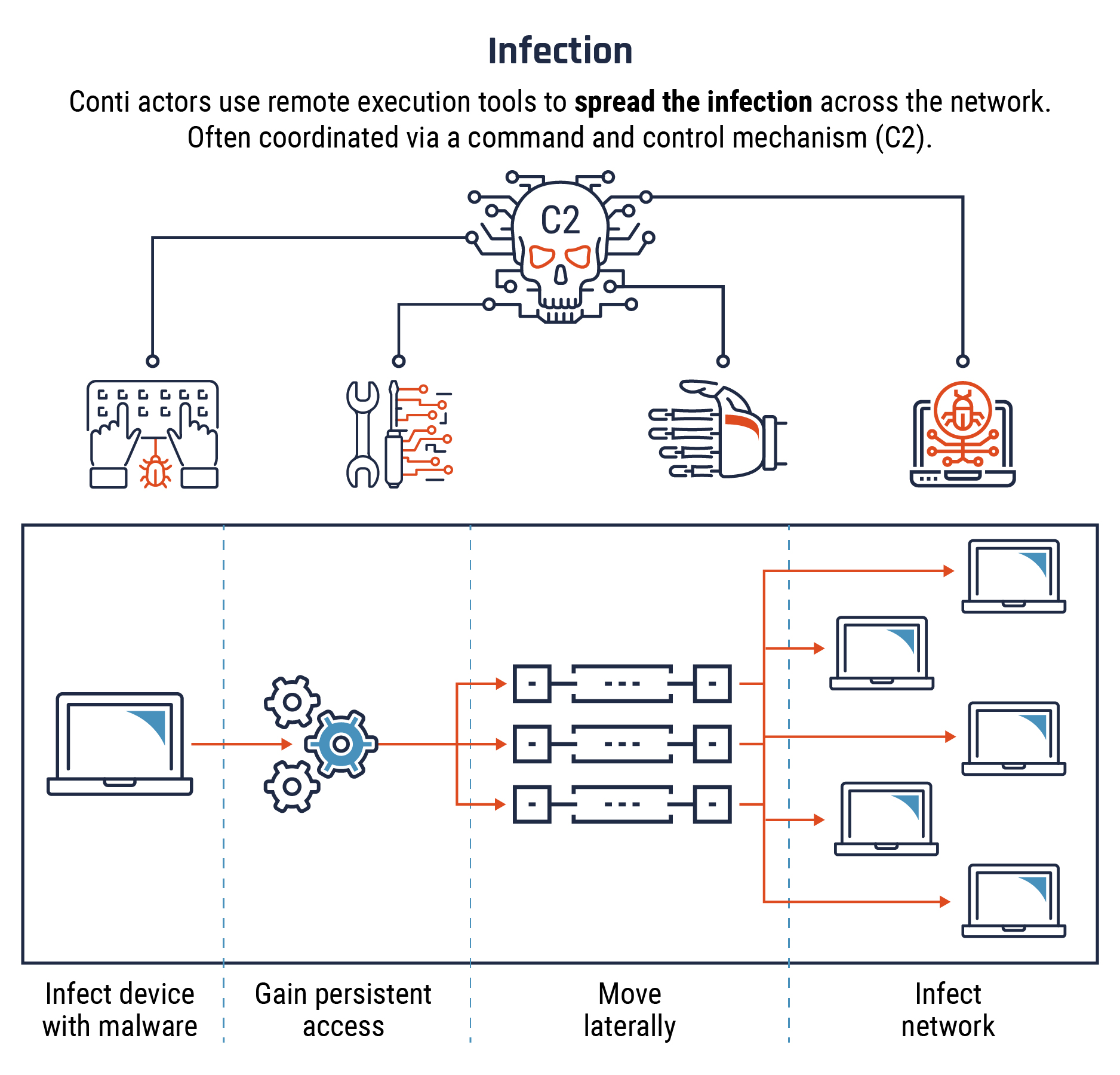
Long description - Stage 3: Infection
Once the first device is infected with malware, Conti actors will often install Cobalt Strike software as a command and control (C2) mechanism to coordinate the next phase of the attack.
They exploit unpatched vulnerabilities and often use tools already available on the victim network to gain persistent access.
They use remote execution software (such as PSExec and Remote Desktop Protocol) to move laterally across the victim network, obtaining credentials and escalating privileges without triggering anti-virus software.
This process allows them to spread the infection to all connected devices on the network.
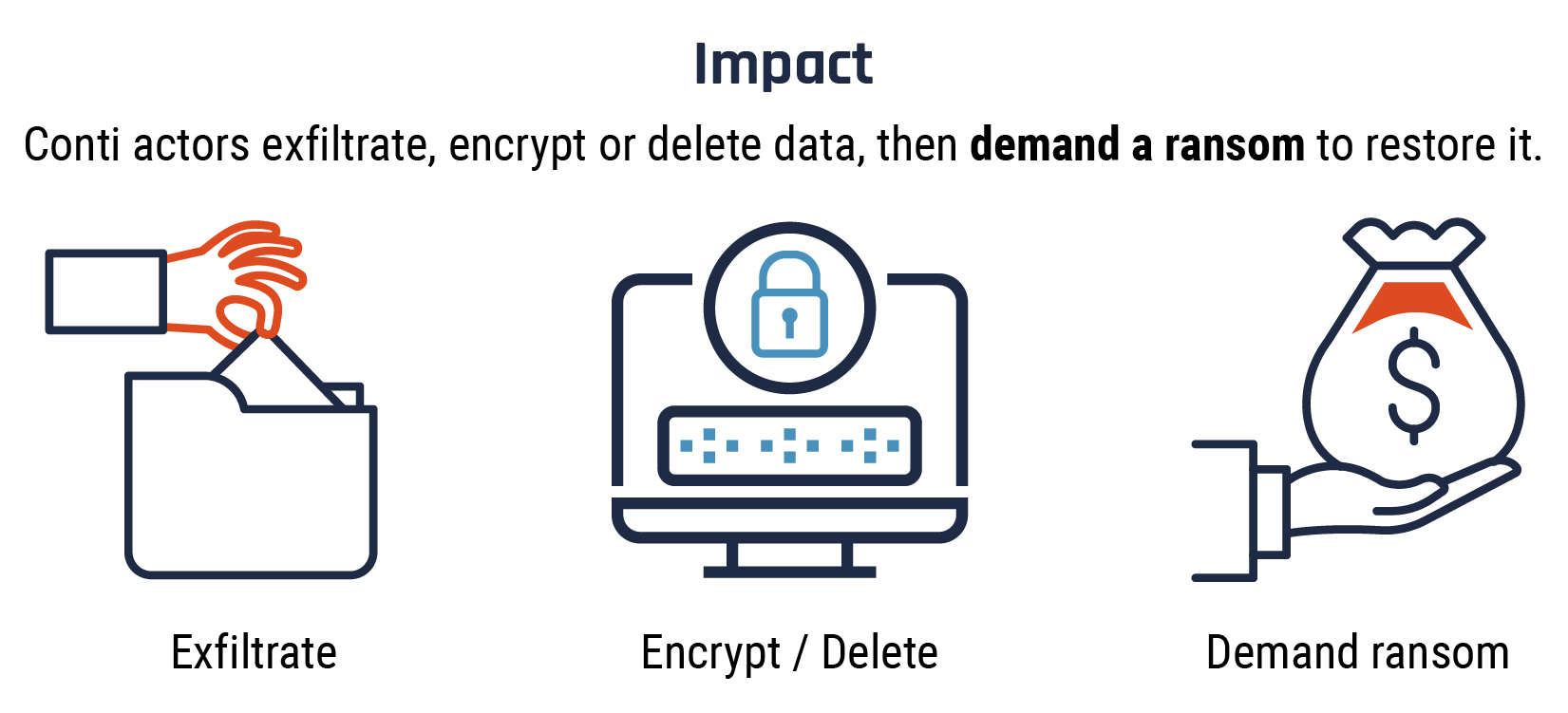
Long description - Stage 4: Impact
At this point, the Conti actors deploy the ransomware, exfiltrating (stealing), deleting or encrypting the victim's sensitive data.
They employ a double extortion technique in which they demand a ransom to restore the encrypted data, while threatening to leak it publicly if the ransom is not paid. They may in fact have already deleted the data, but the victim does not know that.
Facts and figures
Since January 2020 Conti has leaked several hundred gigabytes of data stolen in over 450 cyber attacks against Canadian and international organisations.Footnote 2 This is based on information from Conti’s own “Ransomware Leak Site”. We assume that many more victims have paid ransom without having their data published online.
Conti has publicly claimed to have compromised and stolen data from at least 24 Canadian victims so far in 2021. More than half of those belonged to the machinery, professional services, real estate, and specialty retail sectors.
As of September 2021, the Conti group’s average ransom payment is $373,902 USD. Footnote 3
Conclusion
The Conti group is one of the most sophisticated ransomware groups in operation. However, at every step of this process, there are cyber security tools and practices that can prevent or mitigate the impact of ransomware attacks.
You can find further resources on ransomware, including how to defend against it, on the Cyber Centre’s dedicated ransomware page.
Guidance for organizations
Guidance for all Canadians
Additional resources
- Baseline cyber security controls for small and medium organizations
- Cyber security at home and in the office - secure your devices, computers, and networks (ITSAP.10.00.007)
- Cyber security considerations for consumers of managed services (ITSM.50.030)
- Developing your incident response plan (ITSAP.40.003)
- Developing your IT recovery plan (ITSAP.40.004)
- Guidance on Defence in Depth for Cloud-Based Services (ITSP.50.104)
- Have you been hacked? (ITSAP.00.015)
- How updates secure your device (ITSAP.10.096)
- Internet of Things Security for Small and Medium Organizations (ITSAP.00.012)
- Offer tailored cyber security training to your employees (ITSAP.10.093)
- Preventative security tools (ITSAP.00.058)
- Protect your organization from malware (ITSAP.00.057)
- Protecting your organization when using Wi-Fi (ITSAP.80.009)
- Secure your accounts and devices with multi-factor authentication (ITSAP.30.030)
- Tips for backing up your information (ITSAP.40.002)
- Top 10 IT security actions to protect Internet connected networks and information (ITSM.10.089)
Report a cyber incident
Reporting a cyber incident helps the Cyber Centre keep Canada and Canadians safe online. Your information will enable us to provide cyber security advice, guidance and services.
Get Cyber Safe
Get Cyber Safe is a national public awareness campaign created to inform Canadians about cyber security and the simple steps they can take to protect themselves online.
