Overview of cyber threat to Canada from Iran
On June 13, 2025, the State of Israel (Israel) launched military strikes against the Islamic Republic of Iran (Iran). On June 22, 2025, the United States (U.S.) carried out precision airstrikes on Iranian nuclear facilities.
After the U.S. operation against Iran, the U.S. Cybersecurity and Infrastructure Security Agency, the Federal Bureau of Investigation, the Department of Defense Cyber Crime Center, the National Security Agency, and the Department of Homeland Security warned of potential retaliatory cyber threat activity against U.S. critical infrastructure and other U.S. entities by Iranian-affiliated cyber actors.Footnote 1
It is very unlikely that Canada’s critical infrastructure and other Canadian networks are a priority target for retaliatory Iranian cyber threat activity. Canada was not a party to the U.S. and Israeli strikes against Iran. However, we assess that Canada would likely be an indirect or collateral victim of Iranian cyber threat activity that is intended to target the U.S. In addition, Iran will likely continue to engage in cyber-enabled transnational repression against individuals in Canada that the Iranian regime considers a threat, especially those advocating for regime change in Iran.
Threat activity
- Iranian state-sponsored cyber threat actors conduct disruptive cyber-enabled information operations to further Iran’s geopolitical objectives and the regime’s interests. Iran has developed a network of hacktivist personas and social media channels that exploit these disruptive events to intimidate Iran’s opponents and shape public opinion.Footnote 3
- Iranian state-sponsored cyber threat actors opportunistically target poorly secured critical infrastructure (CI) networks and internet-connected devices around the world, including those associated with the water and energy sectors.Footnote 4 Iranian cyber threat actors have performed denial of services attacks, attempted to manipulate industrial control systems, and accessed networks to encrypt, wipe, and leak data.Footnote 5
- Pro-Iran hacktivists conduct cyber threat activity against Iran’s rivals, but often overstate their impact. In response to the U.S. airstrikes on Iranian nuclear sites, pro-Iran hacktivist groups claimed to have conducted distributed denial-of-service (DDoS) attacks against websites associated with the U.S. military, U.S. defence companies and U.S. financial institutions.Footnote 6
- It is very unlikely that Canada’s critical infrastructure and other Canadian networks are a priority target for retaliatory cyber threat activity by Iranian state-sponsored cyber threat actors or pro-Iran hacktivists. However, Canada would likely be an indirect or collateral victim of Iranian cyber threat activity that is intended to target the U.S. This threat is elevated due to North American interconnectivity in key CI sectors, such as energy and transportation.
- Iranian cyber-enabled transnational repression will likely remain a threat to Canada. Iranian state-sponsored cyber threat actors likely conduct cyber espionage against individuals in Canada that the Iranian regime considers a threat, such as political activists, journalists, and human rights advocates.Footnote 7 In the aftermath of the conflict, we assess that Iranian cyber threat actors will likely target opponents abroad, especially those advocating for regime change in Iran.Footnote 8
Between November 2023 and January 2024, an Iranian Revolutionary Guard Corps (IRGC) cyber unit using the persona CyberAv3ngers conducted a global campaign that targeted and defaced poorly secured, Israeli-made devices used in critical infrastructure. One victim was a municipal water authority in the U.S. that used default passwords.Footnote 2 This activity was likely conducted in response to the Israel-Hamas conflict.
Characteristics of Iranian cyber threat activity
Compelling social engineering
Iranian cyber threat groups are particularly sophisticated in combining social engineering with spear phishing, using these efforts to target public officials and gain access to government networks and private sector organizations globally.Footnote 9 Iranian social engineering efforts focus on using professional interactions on social media platforms to gain information about organizations related to Iran’s political, economic and military interests, particularly in the aerospace, energy, defence, security, and telecommunications sectors. Footnote 9
Exploiting known vulnerabilities
Iranian cyber threat actors exploit known vulnerabilities to gain initial access to systems, and then leverage this access for follow on operations such as data exfiltration or encryption, ransomware, and extortion.Footnote 10 Iranian cyber threat actors opportunistically identify targets using publicly available scanning tools to search for internet-exposed systems with vulnerable configurations, for example devices using default or weak passwords and without multi-factor authentication.Footnote 11
Disruptive and destructive cyber attacks
Iranian cyber threat actors typically conduct DDoS attacks and website / device defacements to temporarily disrupt target networks. They also deploy ransomware and destructive wiper malware and conduct hack-and-leak operations against compromised targets.Footnote 12
Useful resources
Refer to the following online resources for more information and useful advice and guidance.
Reports and advisories
- Canada’s threat assessments
- Advisories and partner publications
Advice and guidance
- Cyber Security Readiness Goals (CRGs): Securing Our Most Critical Systems
- Cross-Sector Cyber Security Readiness Goals Toolkit
- Security Considerations for Edge Devices
- Security considerations for your website
- Top 10 IT security actions to protect Internet connected networks and information
- Top 10 IT security action items: No.2 patch operating systems and applications
- Protect your organization from malware
- Secure your accounts and devices with multi-factor authentication
- Defending against distributed denial of service (DDoS) attacks
About this document
Contact
For follow up questions or issues please Canadian Centre for Cyber Security (Cyber Centre) at contact@cyber.gc.ca.
Assessment base and methodology
The key judgements in this assessment rely on reporting from multiples sources, both classified and unclassified. The judgements are based on the Cyber Centre’s knowledge and expertise in cyber security. Defending the Government of Canada’s information systems provides the Cyber Centre with a unique perspective to observe trends in the cyber threat environment, which also informs our assessments. CSE’s foreign intelligence mandate provides us with valuable insight into adversary behavior in cyberspace. While we must always protect classified sources and methods, we provide the reader with as much justification as possible for our judgements.
Our key judgements are based on an analytical process that includes evaluating the quality of available information, exploring alternative explanations, mitigating biases and using probabilistic language. We use terms such as “we assess” or “we judge” to convey an analytic assessment. We use qualifiers such as “possibly”, “likely”, and “very likely” to convey probability.
The contents of this document are based on information available as of June 27, 2025.
The chart below matches estimative language with appropriate percentages. these percentages are not derived via statistical analysis, but are based on logic, available information, prior judgements, and methods that increase the accuracy of estimates.
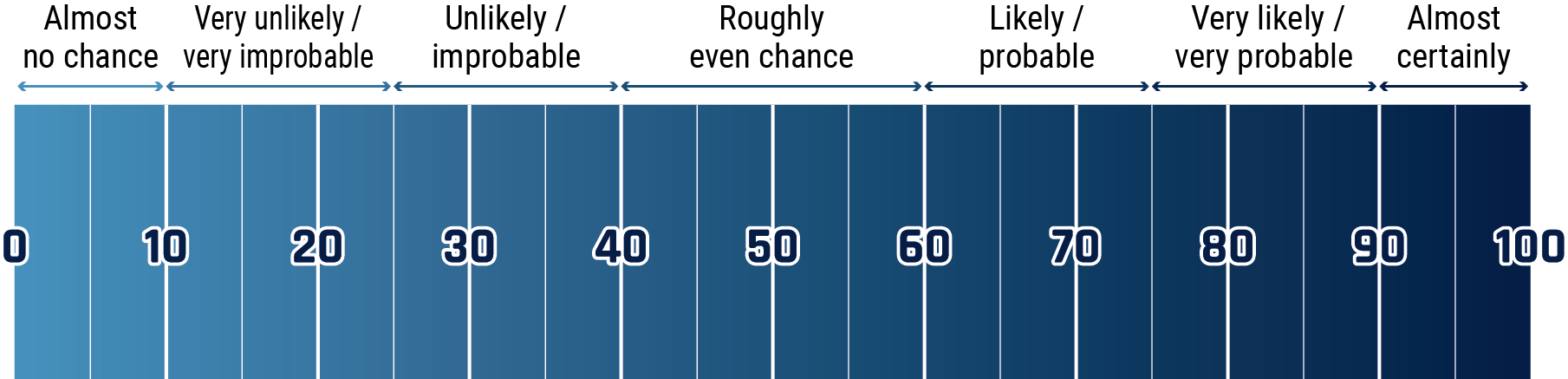
Long description - Estimative language chart
- 1 to 9% Almost no chance
- 10 to 24% Very unlikely/very improbable
- 25 to 39% Unlikely/improbable
- 40 to 59% Roughly even chance
- 60 to 74% Likely/probably
- 75 to 89% Very likely/very probable
- 90 to 99% Almost certainly